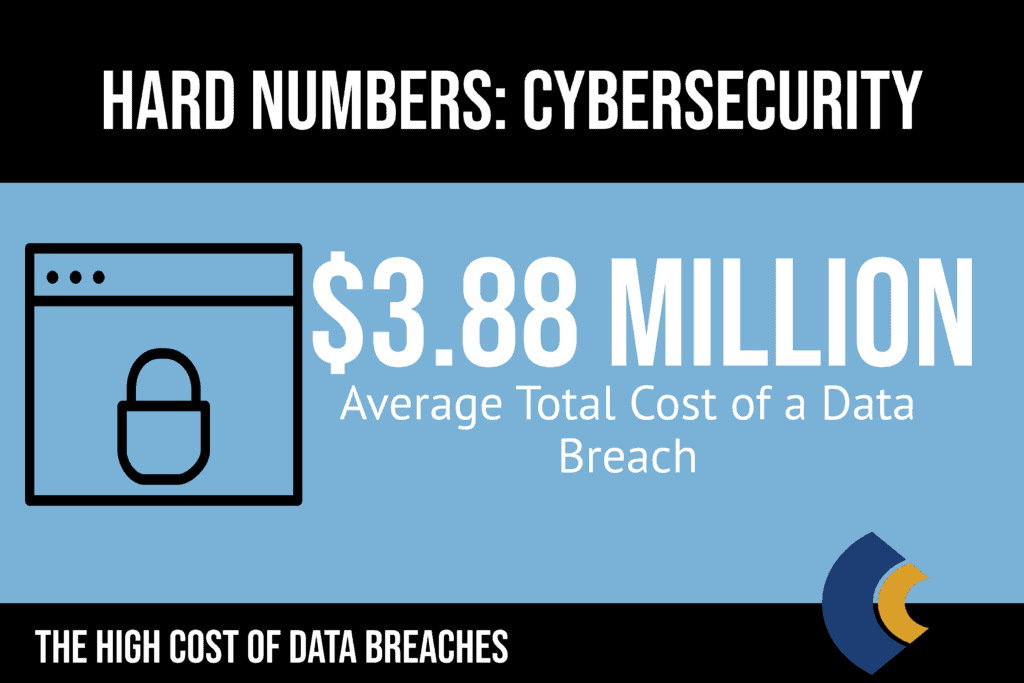
In 2020, The Ponemon Institute, in conjunction with IBM Security, generated the 14th annual report regarding the Cost of Data Breaches for 2019. This report includes the findings from interviews with more than 500 global companies in 16 countries (covering more than 3,000 interviews) who had experienced a data breach between the dates of July 2018 and April 2019.
First, though, let’s define the event –
A data breach is an action/event during which the contents (name and personal data, etc.) of an electronic record (or paper record) has been put at risk. The record, which contains sensitive & private data, can be a medical or financial record, among others.

It is essential to notate that not every data breach creates the same recovery costs. Malicious attacks (sourced by an insider or not) were materially different from a data breach caused by a human error or system glitch. Malicious attacks accounted for the majority of data breaches in 2019.
According to the above-referenced report, of the 17 industries included in the study, university data breaches rank as follows –
- 7th, with an average total cost of each data breach at $4.77 million.
- 8th, with an average cost per record of $142, with the healthcare in the unenviable position of ranking first with an average cost of $429 per record.
Data Breaches in Higher Education
For hackers, colleges and universities are quite valuable because of the massive amounts of data and information they store regularly. The data includes students’ grades and even more personal information in terms of employee data (bank account info) or social security numbers for both employees and enrolled students. Because of the potential losses – in terms of recovery dollars and reputation – security regarding higher education data breaches has become a top priority at most higher education institutions.
According to the Identity Theft Resource Center, these are the statistics for the most recent university, and college data breach successful hacks –
- 2017 – 129 education breaches that put 1.4 million records at risk.
- 2018 – 76 education breaches that put 1.4 million records at risk.
- 2019 – 104 education breaches that put 2.2 million records at risk.
The exact costs regarding a data breach will depend on several factors. These include –
- The depth and extent of the data breach.
- The time it takes to identify and then contain the data breach.
- The costs involved in contacting potential victims and any resulting legal actions.
The reality is that in today’s modern, tech-heavy world, securing data has become a fundamental priority for most businesses in the private, financial, medical, government, and education sectors, among others. Maintaining databases of personal information is clearly a threat to any company or organization.
Cyber Attacks That Target Higher Education
Hackers target companies and institutions of higher education in several fundamental ways.
The first method is to access private, sensitive information by hacking passwords using electronic tools that can generate millions of password options in only seconds – likely breaking the passcode in that time.
The second method used by hackers and criminals is the implementation of malware, which is available in several types –
- Malware is developed to meet a specific goal, like collecting information (operating in the background) from a user’s browser or commanding the CPU to work to the benefit of the hacker.
- Additional malware can corrupt the computer system or release ransomware or viruses to delete files maliciously.
- Ransomware is considered quite impactful because it can potentially hit any area of a company or organization. Ransomware attacks are often fast attacks.
The third category of electronic tools used by hackers is social engineering, of which phishing is the most common. Phishing occurs when fraudulent emails (or even social media messages) are sent that supposedly represent a valid company – typically attached to an urgent request about a problem with the user’s account. Phishing works off of volume.
Social engineering is a method in which a hacker pretends to be another person or company, and in doing so, tracks the user into –
- Releasing personal data.
- Permitting access to restricted areas.
- Downloading malicious attachments.
As noted previously, the nature of higher education institution networks makes their networks even more vulnerable to cyber hacking. In addition, these are the other common reasons for security breaches which include identifying vulnerabilities in the university’s system, stealing data, and/or modifying information.
- False authentication – cyber hackers can utilize data extracted from digital communications to gain access to protected and secure areas of the network.
- Hijacking – hijacking occurs when a cyber attacker assumes control of the digital communication between one or more individuals.
- Spoofing – spoofing occurs when a cyber attacker sends out emails that impersonate a known entity or trust individual.
- Sniffing – Sniffing is a bit more subtle than spoofing. Sniffing happens when a cyber hacker takes over network traffic.
- The Man-in-the-middle – the man-in-the-middle is similar to hijacking in that cyber attackers intercept digital communications in order to read the communication or modify the contents of the communication. The hallmark of the man-in-the-middle is that neither party to the communication has any knowledge about the data being intercepted. The cyber hacker can then use the information obtained in the interception to falsify an authentication for access to a restricted area on the network. Neither party knows about the interceptions, which the hacker can use for false authentications.
It is also important to note that disgruntled, terminated, or dishonest employees can become a huge data breach security risk. Malicious employees may be motivated to access private information as a matter of revenge or financial gain.
Motives for Attacking Higher Education
The reality is that most expert hackers know how to stake out a soft target, and students are typically too busy with school and their social lives to pay much attention to cybersecurity threats regarding their personal information.
The higher education sector of the economy offers cyber hackers is quite appealing to most cyber hackers. Schools maintain large amounts of personal and sensitive data that cyber criminals crave regarding staff members, students, alumni, plus all of the information included in the university’s proprietary research and any valuable intellectual property. In addition, schools manage huge amounts of money with regard to tuition and funding for research projects.
The reasons cyber hackers steal information and data range from the uninformed and curious to those who wish to exact revenge from an economic, political, or financial perspective. Absconding with stolen research data is often quite profitable as it can be sold on a black market to the highest bidder. Some cyber criminal experts state that stolen data has grown to become more profitable than the crime of drug-trafficking.
Significant Examples of Higher Education Breaches
Unfortunately, there is no shortage regarding the number of cybersecurity threats experienced by institutions of higher education. Cyber hackers find schools and universities’ databases particularly appealing because they are typically complex and extensive, which makes these networks quite tricky to protect.
The first significant example of a higher education data breach occurred in 2002 when Yale University was hacked by offenders from Princeton looking to lift data regarding Yale’s admissions decisions. A few recent cyber hacking events highlight the different ways hackers enter systems and use the breach in a variety of ways.
Let’s review a few significant data breaches in higher education that happened recently –
2006 – The University of California Los Angeles (UCLA)
In the fall of 2005, the University of California, at LA, was hit by a cyber-attack that permitted access by a cyberhacker to private data of more than ¾ of one million former & current students, staff, and faculty. The database that was hacked had information regarding social security numbers, birthdates, names, and addresses. Potential victims were notified and warned (about a potential for identity theft) in spite of the fact that the school said they had not found any evidence of misuse.
2011 & 2013 – Maricopa County Community College District – Arizona
The Maricopa County Community College (MCCC) District encompasses ten community colleges. The community college system has been the victim of two higher education data breaches.
- January 2011 – the FBI notified MCCC of a data breach that impacted about 400 individuals. The FBI found private information on the dark web that was for sale and warned the school district that its systems were not properly secured. An Arizona auditor found ten months that the school had terminated employees who still had access to the system.
- 2013 – Despite numerous warnings, MCCC was hacked again in 2013, when 2.5 million students/staff/vendor information (both former and current) was put at risk.
2014 – The University of Maryland
This public ivy school fell victim to a data breach that exposed more than 300,000 records. The school’s administrators understood just how sophisticated these hackers had to be as they had to bypass several firewalls and multi-layers of security defense. The university’s Chief Information Officer noted that the attacks were not opportunistic (without human error) as the cyber hackers had to pick several locks to enter the database.
2017 – Washington State University – Social & Economic Science Research Center
Washington State University (WSU) had a hard drive stolen from its Social & Economic Science Research Center that was the back-up storage unit. This hard drive contained sensitive demographic data from more than 1 million people. Two years later, WSU reached a settlement (total outlay $4.7 million) where the victims of the theft could receive upwards of $5,000 to reimburse them for credit reports, monitor services, or out-of-pocket expenses.
A breach of this type highlights the importance of all higher learning institutions (and K-12 schools) to implement guidelines to ensure sensitive and private data is protected, with no risk of anything being stolen physically or online.
2019 – Georgia Institute of Technology
In the spring of 2019, the Georgia Institute of Technology (Georgia Tech) fell victim to a higher education data breach. A breach of more than 1,250,000 million records – that included previous or current students, staff members, student applicants, and faculty members who were impacted by the unauthorized access to Georgia Tech’s web application.
The information that had been compromised by this breach included social security numbers, birthdates, names, and addresses, among other pertinent but private data.
Since this breach occurred, Georgia Tech has implemented essential steps to help those who were impacted by providing –
The school has taken measures to ensure all students and faculty members have had their private information put at risk be fully aware of the potential problems that may occur from this breach.
2019 – Graceland University – Missouri
Graceland University reported several incidents of unauthorized access to current employee’s email accounts. The school states that the hacking events happened on 3/29 and then the Month of April, and again from 4/12/2019 to 5/1/2019. Personal information for some individuals who had interacted with these hacked accounts had their personal data put at risk. The information that may have been stolen included –
- Full names.
- Social Security numbers.
- Home and email addresses.
- Telephone numbers.
- Salary and other financial information regarding enrollment possibilities.
2019 – Missouri Southern State University
Missouri Southern State reported a potential phishing cyber-attack to the Missouri & Vermont Attorney General in January 2019. The school hired forensic investigators to research the cybersecurity incident and to facilitate a massive block of all email exploitation, including a full reset of all passwords of all employee accounts. The school finally notified those who may have had their names and social security numbers compromised by the cyberattack at Missouri Southern State University (MSSU).
MSSU offered all those who were impacted by the security breach no-cost credit monitoring services for two years.
2019 – Pearson
Pearson, an educational software developer, experienced a data breach in 2019 when the FBI notified the company of a potential breach of its web platform. Pearson discovered that about 12,900 accounts from various schools and universities had been affected, which likely represented thousands of individual and staff accounts for each school or university. As such, the exact number was not known but was likely tremendous. The amount of information exposed was large and included –
- Students –
- Names and addresses of students.
- Student dates of birth.
- Student ID numbers.
- Student email addresses.
- Staff & Faculty Members –
- Names and addresses of faculty and staff members.
- Faculty and staff members’ dates of birth.
- Faculty and staff members’ email addresses.
- Faculty and staff members’ job titles, among other information.
The breadth and depth of these higher education data breaches vary but offer some sobering reminder as to the dangerous problems that can occur when a cybercriminal can steal various levels of data, like a name, a birthdate, and other personal information that acts as identifiers.
The incidences of cyber-attacks happen at a frightening regularity in the realm of higher education. The above cybersecurity incidents highlight the strong need for Information Technology experts in schools to proactively embrace a stance against potential cyber-attacks by hackers.

The Ways Institutions of Higher Education Can Prevent Cyber Attacks
Combatting cyber-attacks at the college or university level has become a full-time job. In 2015, the VP Provost responsible for Information Technology at Penn State University (PSU) told the NY Times that Penn State faced up to an average of 20 million cyberattacks every day – a typical number for most comprehensive universities. In fact, many of the required steps that are needed to take to mitigate the incidents of data breaches must impact more than simple technology upgrades.
Because colleges and universities operate on an open network that is accessible to both staff and students, cyber hackers have several entry points into any school’s digital network and systems. And because there is a wide variety of sensitive data at potential risk, higher learning institutions are mandated to be proactive and implement protocols and guidelines to prevent future attacks by upgrading their system and by the use of effective threat detection software.
Because these cybersecurity measures and enhancements must comply with a host of rules and regulations, it is challenging to find the balance needed to ensure the system can thwart a security breach while remaining compliant and providing access to those students and staff members who need access.
As such, most schools have been mounting a solid offense in a race to stay one step ahead of the attacks that have yet to occur. Managing cyber vulnerabilities is now a very necessary but expensive endeavor for many schools.
Perhaps one of the biggest challenges for universities and colleges to set up strong security protocols without restricting the culture of openness a school hopes to offer. And while schools are concerned about the potential financial impacts of these cybersecurity breaches, higher learning institutions must also remain concerned about the school’s reputation and the safety of its students and staff.
Prevention is the Best Offense
Schools and universities have begun to implement extensive control policies – like multifactor authentication, that will make it more challenging for unauthorized users to access personal information. Large universities could easily have many hundreds of thousands of accounts and users at any given moment.
Many of the users of a college or university network will use older equipment that may not have the specs and protection required to keep the network safe. As such, these users may leave openings that are vulnerable to cyber hackers and cyber criminals.
Most schools have understood what their systems face and now implement formal IT security policies and the conduct required to remain compliant. Additionally, most schools implement ongoing training for both faculty and students.
The Key to Reducing the Cost of Cyber Security Breaches is Encryption
The process of encryption is one of the most efficient and effective ways to mitigate the cost of a data breach. Encryption is the process that makes valuable digital assets undecipherable, even if a hacker has breached the perimeter of the school’s systems. Encryption provides full protection requires you to keep the keys protected and to apply the encryption to all sensitive data.
Encryption ensures that those users who are authorized have access to the encryption key, whereas anyone else would find the data unreadable. Several studies suggest that using encryption can decrease the cost associated with a data breach by as much as $15 per record.
There are data encryption solutions that are optimized for the many demanding & complex network and computing architectures. Encryption ensures that schools and universities can proactively protect their students, their staff, and faculty members, as well as the school’s data and proprietary research.
Assume a Data Breach Will Happen
Institutions of higher learning must implement a host of policies and guides to ensure information and data remain inaccessible to unauthorized users or cyber hackers. Given the vulnerability of the data within a school or university’s data network and systems, it is imperative that As such, the information technology and cybersecurity employees at the school must answer these types of questions –
- How will cyber threats be detected?
- Who will report cyber threats or suspicious activity, and how should the information be communicated appropriately?
- How will the cyber-attack be contained?
- What steps have been enacted to make sure a similar cyber-attack does not reoccur?
In fact, cybersecurity incident response plans must be tested (and retested) on a regular basis to ensure that the school has the ability to take swift and decisive action.
The Take-Away
The trends of cybersecurity issues provide a greater picture as to the risks faced by higher learning institutions. However, mitigating the impact of these cyber threats requires that IT professionals in post-secondary schools implement best practices that help –
- Identify weaknesses throughout the network.
- Engage network users to comply with guidelines.
- Secure infrastructures and networks.
Universities and schools have realized that they need to proactively implement a well-thought-out data breach strategy and protocol before the issue occurs. As such, it is essential for schools and universities to implement steps to mitigate cybersecurity risks, to protect sensitive data belonging to staff and students, and to preserve the integrity of the institution’s data.
Related:
Best Online Associate’s in Cybersecurity
Best Online Bachelor’s in Cybersecurity
